
Enhancing Threat Visibility and Response Readiness
In today’s threat landscape, monitoring and detection are foundational to a resilient cybersecurity posture. They enable organizations to spot threats in real time, identify anomalies, and respond rapidly to incidents—minimizing potential damage.
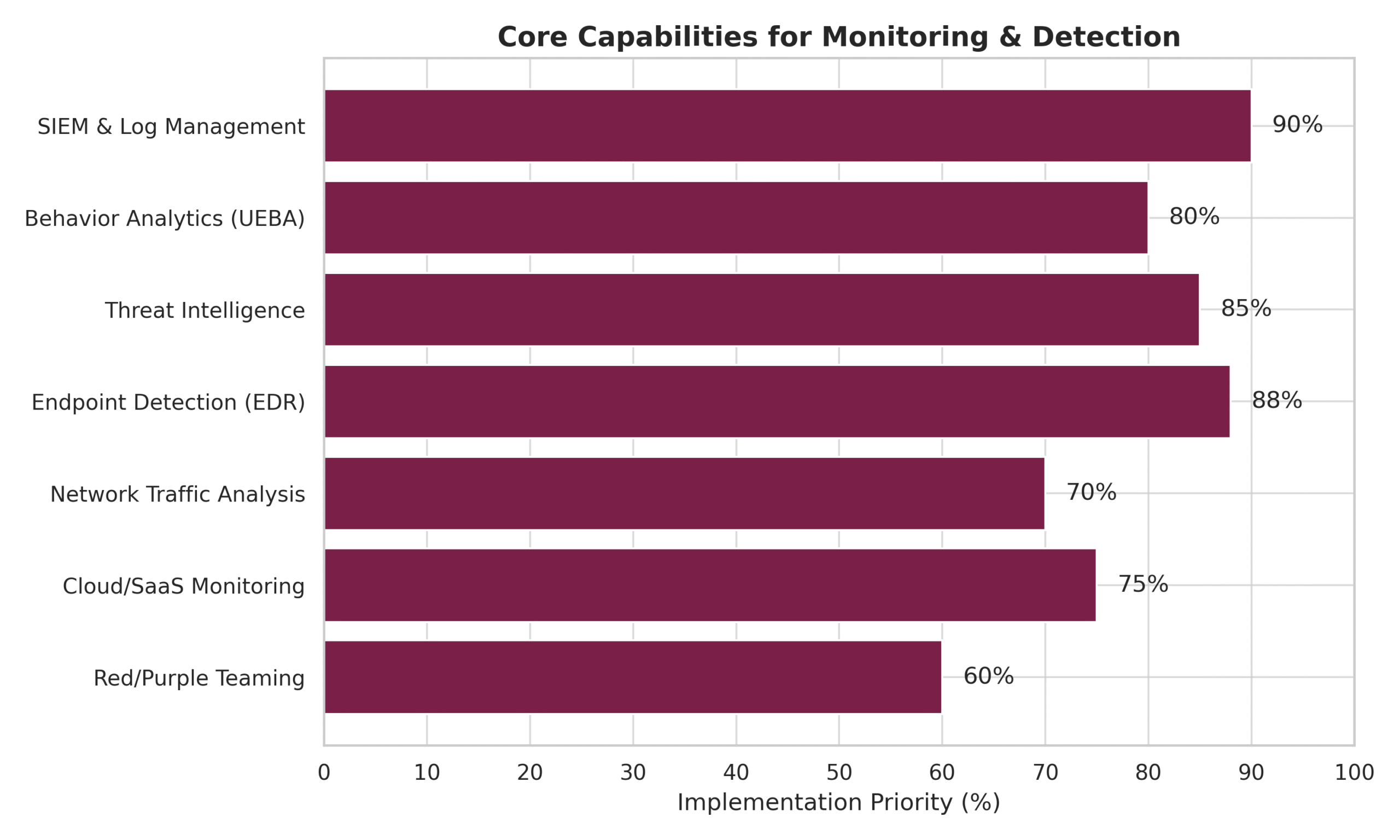
We view monitoring and detection as core pillars within any enterprise security framework. Below is a structured overview of essential components and tools for building robust detection capabilities across hybrid and cloud-first environments.
1. Centralized Monitoring Architecture
Implement a Security Information and Event Management (SIEM) platform to aggregate logs and events across your IT ecosystem. This includes firewalls, servers, endpoints, cloud environments, identity providers, and business applications.
It establishes a unified source of visibility across systems and accelerate threat detection and investigation.
2. Log Management and Normalization
Ingest and normalize log data from disparate sources for consistency in analysis. Enrichment with metadata—timestamps, IP addresses, user identities, actions—enables more precise threat detection and correlation.
3. Real-Time Alerts & Correlation Rules
Configure real-time alerts for suspicious activity such as repeated failed logins, unexpected privilege escalations, or anomalous data exfiltration. Apply correlation rules to link related events across systems, improving accuracy and reducing false positives.
4. Behavioral and Anomaly Detection
Leverage User and Entity Behavior Analytics (UEBA) to detect deviations from normal usage patterns. This helps surface threats like insider abuse, credential compromise, or lateral movement that signature-based systems may miss.
5. Threat Intelligence Integration
Integrate threat intelligence feeds to match activity against known indicators of compromise (IOCs). Enriching alerts with external threat context improves prioritization and response time.
6. Endpoint Detection and Response (EDR)
Deploy advanced EDR solutions such as Microsoft Defender for Endpoint or CrowdStrike. These tools monitor endpoint-level activity, enable threat isolation, and support forensic investigation following an incident.
7. Network Traffic Analysis
Use tools like Zeek, Darktrace, or Corelight to perform deep packet inspection and monitor network behavior for signs of command-and-control, data exfiltration, or lateral movement.
8. Cloud and SaaS Security Monitoring
With the shift to cloud, deploy cloud-native monitoring tools (e.g., AWS GuardDuty, Azure Sentinel) and Cloud Access Security Brokers (CASBs) to monitor workload activity, permissions, and SaaS platform usage for threats or misconfigurations.
9. Red Teaming and Purple Teaming
Test and mature detection capabilities through Red Team exercises (simulated adversary tactics) and Purple Teaming(collaborative exercises between attackers and defenders). These programs reveal detection gaps and drive improvements.
10. Dashboards, Reporting & Continuous Improvement
Consolidate detection metrics into real-time dashboards and periodic reporting. Track meantime to detect (MTTD) and respond (MTTR), and routinely refine detection rules to adapt to evolving threat tactics.
Final Thoughts
Effective monitoring and detection are not one-time implementations—they are living capabilities that evolve with your business and the threat landscape. At Fidantis, we help organizations architect these systems to be proactive, adaptive, and resilient.
If you’re interested in strengthening your monitoring posture or want to assess how your current tools align with your threat profile, let’s connect.