Integrating AI for Effective Governance and Recovery
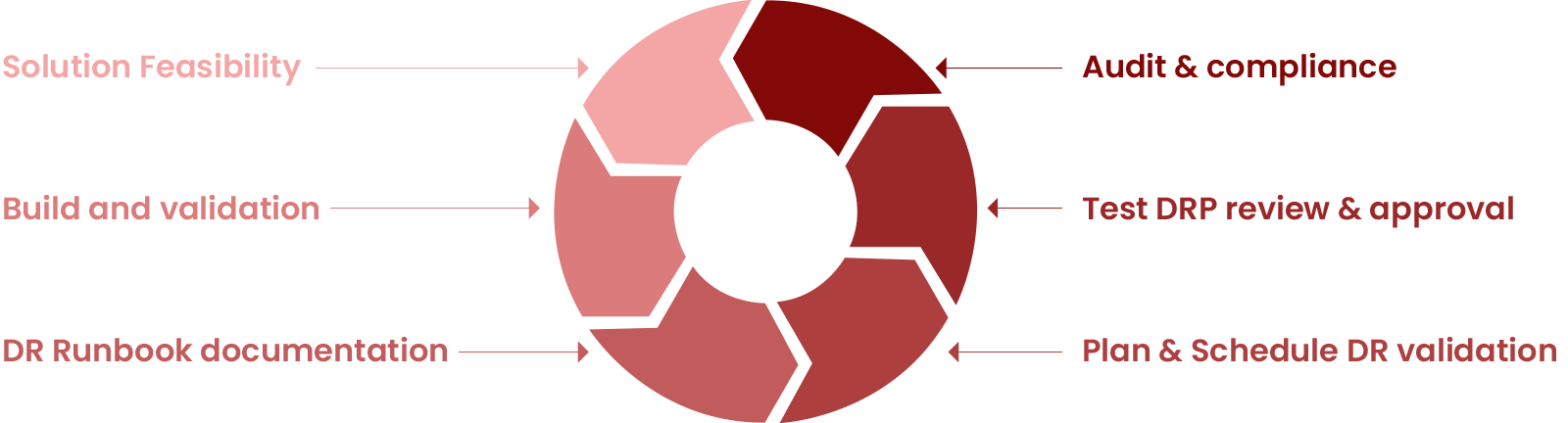
















Streamlining Processes for Greater Efficiency
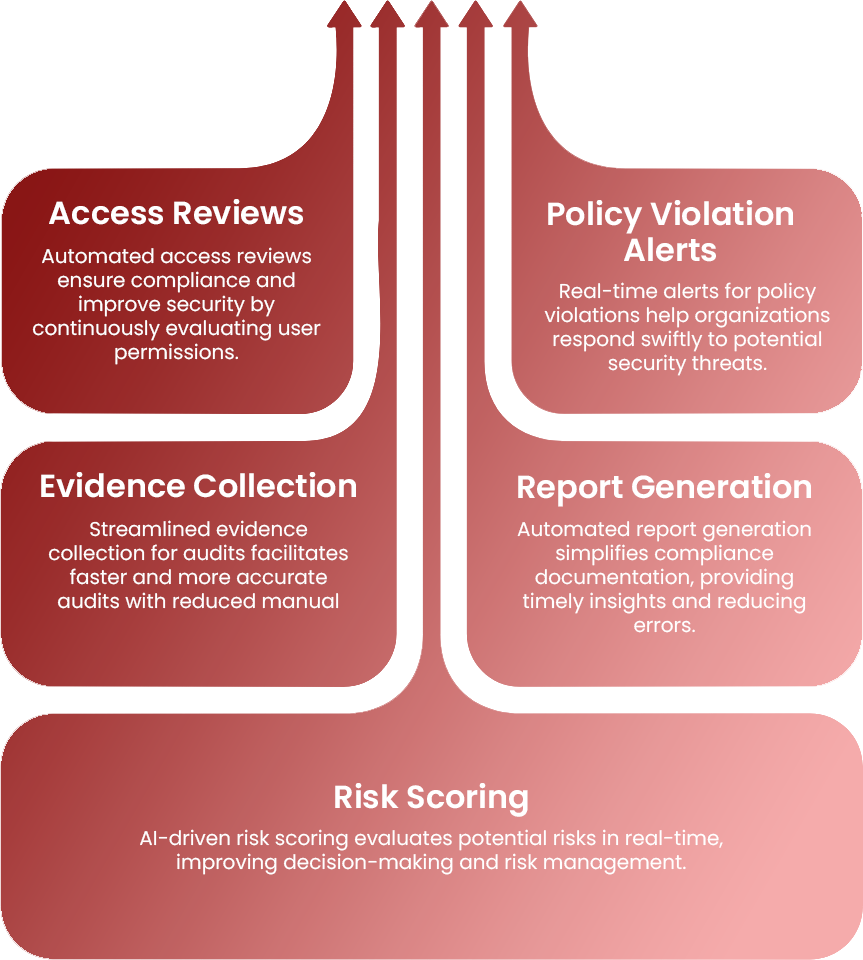
Integrating AI and Automation in Security Operations

Utilizes advanced anomaly detection and graph machine learning to enhance threat intelligence capabilities.
Implements SOAR workflows powered by agentic bots to automate responses to security incidents efficiently.
Minimizes reliance on human analysts by providing round-the-clock automated triage of security alerts.

Implementing zero trust principles ensures that all access requests are verified and authenticated
Utilizing FinOps and Cloud Security Posture Management (CSPM) to optimize cloud costs and manage risks
Establishing compliance guardrails like HIPAA and ISO ensures adherence to industry regulations
Creating secure landing zones using Terraform and Infrastructure as Code (IaC) ensures compliance and security.
Integrating security into CI/CD pipelines enhances application security through SAST and DAST testing.