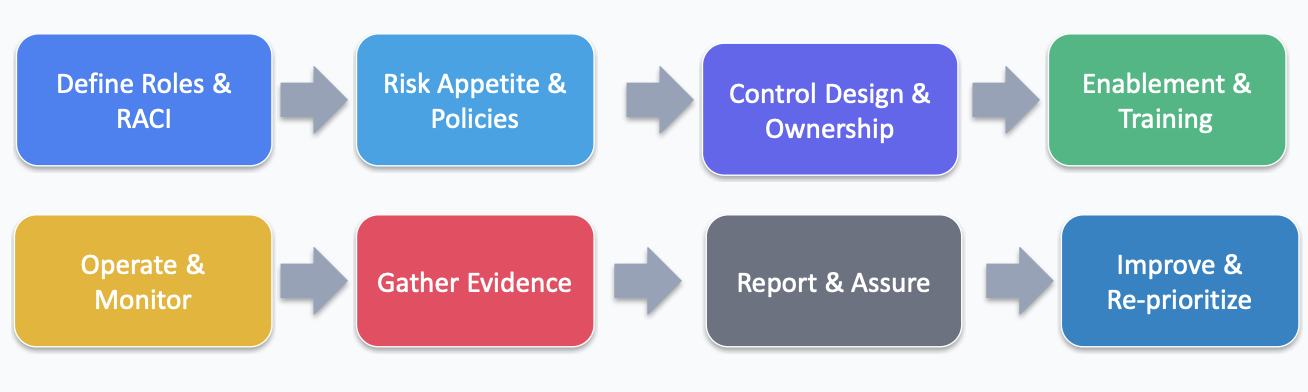
Governance and compliance are foundational to an effective enterprise security framework. They ensure that security policies align with business goals, regulatory requirements are met, and controls are consistently enforced. This document outlines key steps and best practices for managing governance and compliance in a structured, scalable, and measurable way.
1. Establish Security Governance Structure
Define roles and responsibilities for cybersecurity leadership. Appoint a CISO, form a governance committee, and align security strategy with business objectives.
2. Develop and Maintain Security Policies
Create core policies such as Acceptable Use, Access Control, Data Classification, and Incident Response. Review policies annually and store them in a central repository.
3. Identify Applicable Compliance Requirements
Determine which laws and frameworks apply (e.g., GDPR, HIPAA, NIST, ISO 27001) and map them to internal policies.
4. Conduct Risk & Compliance Assessments
Perform internal audits, gap assessments, and third-party evaluations. Use tools to track risks and findings.
5. Document Controls and Evidence
Maintain documentation for controls, including audit logs, access reviews, training records, and test results.
6. Implement Security Awareness and Training
Deliver annual training and role-specific education. Use phishing simulations and track policy acknowledgment.
7. Automate Governance Processes Where Possible
Automate compliance workflows, evidence collection, and reporting with GRC tools or integrations.
8. Monitor & Report Metrics to Leadership
Track metrics such as policy violations, audit findings, and training completion. Use dashboards to communicate risk posture.
9. Review and Improve Regularly
Continuously update governance processes and controls to align with new threats, technologies, and regulations.
Governance Operating Model