
Risk management is the backbone of a resilient enterprise security program. Its purpose is to safeguard critical systems and data by systematically identifying, assessing, mitigating, and monitoring risks—while ensuring alignment with business goals and compliance obligations.
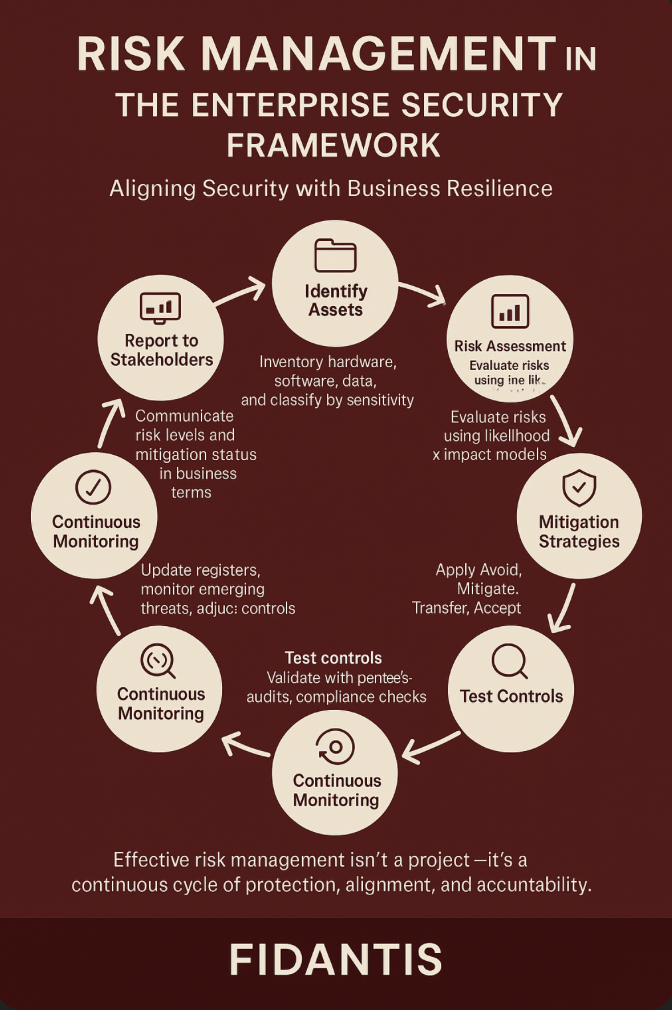
1. Identify Information Assets
● Build a complete inventory of hardware, software, applications, and data repositories.
● Classify assets by sensitivity (e.g., public, internal, confidential, restricted).
Map where critical data resides and how it flows across systems.
2. Identify Threats and Vulnerabilities
● Catalog external threats (malware, phishing, ransomware, DDoS) and internal threats (insider misuse, human error).
● Detect vulnerabilities such as outdated software, weak configurations, unpatched systems, or third-party risks.
3. Conduct a Risk Assessment
● Evaluate risks by analyzing likelihood and impact.
● Use structured methods such as a risk matrix, heat map, or scoring model.
● Prioritize high-impact/high-likelihood risks for immediate action.
4. Maintain a Risk Register
● Record each risk along with:
● Risk owner
● Existing controls
● Residual risk level
● Remediation plan and timeline
● Keep this as the single source of truth for risk tracking.
5. Define and Implement Mitigation Strategies
● Apply the four standard treatment options:
● Avoidance – eliminate the activity creating risk.
● Mitigation – reduce likelihood/impact through stronger controls.
● Transfer – shift risk via insurance or third-party contracts.
● Acceptance – acknowledge the risk if it falls within tolerance.
6. Test Security Controls
● Verify the effectiveness of controls through penetration testing, red teaming, audits, and compliance assessments.
● Address gaps uncovered during testing with corrective actions.
7. Continuous Monitoring and Review
● Update the risk register regularly as new threats emerge or business priorities change.
● Use automated monitoring tools to detect anomalies, intrusions, and misconfigurations in real time.
8. Report to Stakeholders
● Provide executives and board members with clear, business-oriented reporting.
● Highlight:
● Current risk levels
● Business impact of potential disruptions
● Progress on remediation and risk reduction
● Translate technical details into actionable insights for decision-making.